Python Exploitation Logic
Date : 10 Jan 2020
Author: mucomplex
On this topic, I will teach simple python trick to handle payload or data during exploit development.Most common mistake new exploit developer is data handling,for example type conversion,padding, raise exception and etc.
Payload Splitting
This useful when you need to cut payload to get some informational value,eg: ip address and port , stack cookie, rbp (base pointer) , return address
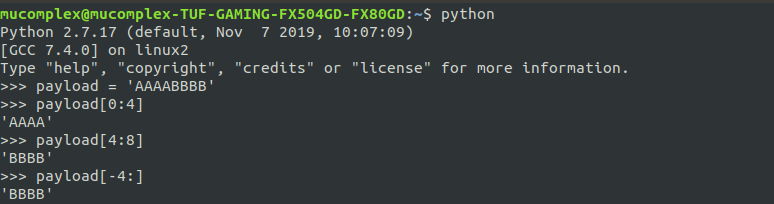
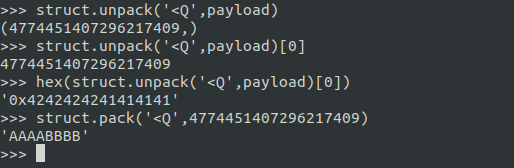
Unpack data
During receive packet request ( process.recv(1024) ) , data need to be unpack first for logical use.(eg:xor,add,sub,div and etc). without this, you will be headache to handle type conversion and even implement some of beginner new algorithm to handle this kind of data.
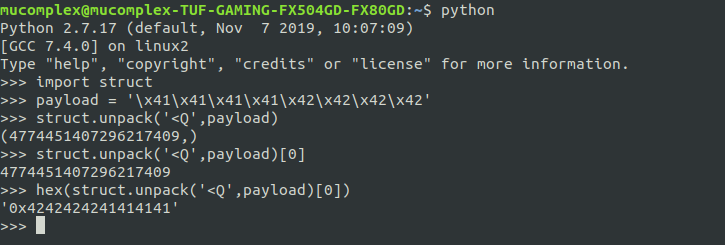
Logical process
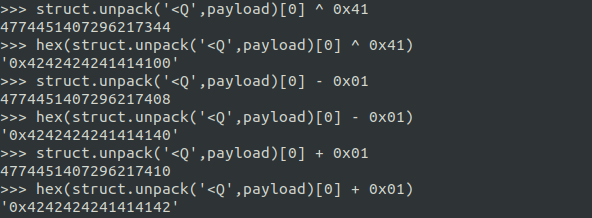
Encoder
You can’t simply use function hex(),Exception raise will be hex() argument can’t be converted to hex.you need to use proper calling encoding function for string.
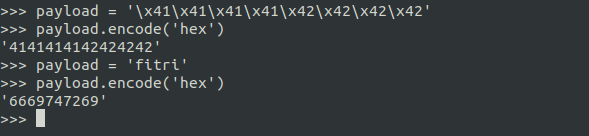
Pack data
Once you ready to send your data/payload . It should be packed the data/payload first.
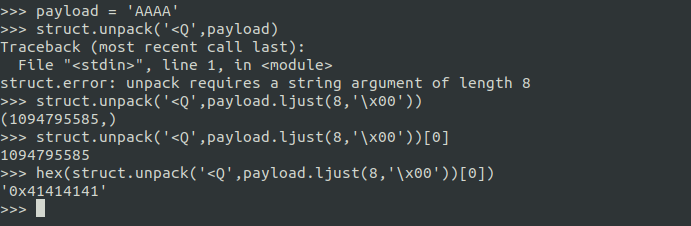
length adjust
Sometimes, packet that you receive is short that expected value.for example packet receive after leak some information is 6 byte, 2 byte short.Usually short byte is null byte,Carriage Return (CR) or Line Feed(LF).It’s proper for you to implement padding on your data/packet.
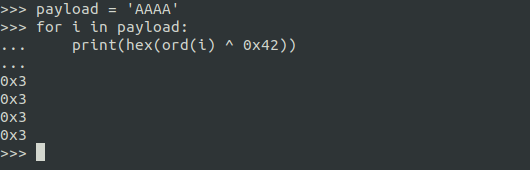
Encode and decode looping logic
You can simply manipulate each byte of your payload by looping logic.
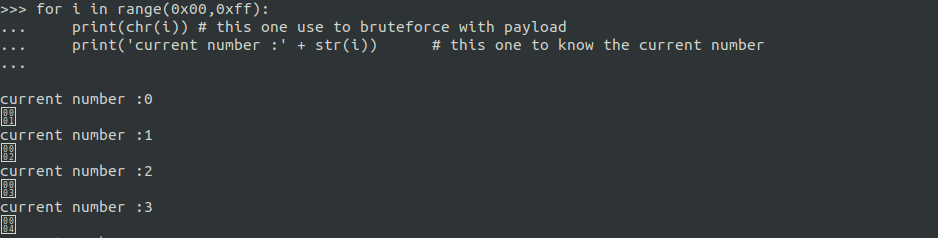
Brute force logic
All of this is based on my personal experience during exploit development.It essential enough to strengthen your coding skill. Good bye~ :D